First impression is everything. Want to have that everlasting first impression on your users and customers using your online service? You have landed up at the correct place!
For an online service/application, the first step is logging into it and if this is smooth then you have great chances to have gained the trust of your clients and customers.
How easy is it to establish secured business collaborations online? Or you want to give access to a specific service to selected employees. When you are working in your organization, it’s not just you or your employees, but there are collaborations at different levels. But now since we are shifting more and more to an online environment these collaborations are also becoming online. So, one very important question that might come to your mind is how secured are these online collaborations for your organization’s confidential data and plan? There’s a secure and easy way for collaborations out there for you.
Microsoft understands your dilemma and has a solution to your problem in the form of Azure AD. Azure AD allows different methods for you to give access to people outside your organization.
What are the ways out there to do this? Another very common but important question is whether this is a tough and complicated process? Well, we have got the answers to all these questions.
There are two ways to provide access to people outside your organization using Azure AD – B2B (Business-to-Business) and B2C (Business-to-Customer). While B2B authentication has its own uses, B2C may be a more suitable choice as compared to B2B. Why? Let’s see.
As we move further with the features and authentication process for each, you will realize that in B2B you can allow different levels of administrative and security roles in different environments for your invited users.
While in B2C you can let the user sign up to use your tenant services or you can also assign them security and administrative roles for collaboration. This may or may not allow them to make changes to your tenant.
Azure AD B2B is easy to understand and set-up for use, but Azure AD B2C is more user-friendly. B2C allows you also to make your repository of customer journeys sorted to a great extent.
Let’s look into its features and then that would give you more insight over the differences and benefits of B2C over B2B authentication type.
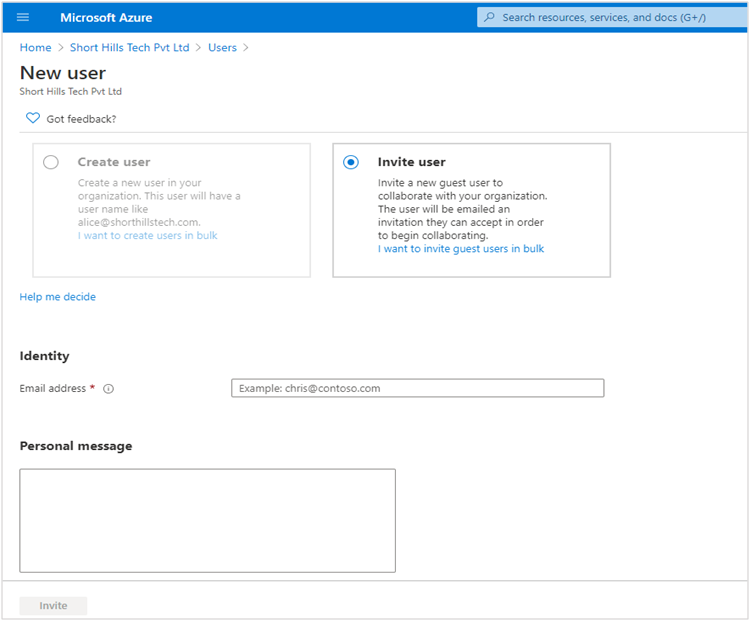
[Inviting users for collaboration]
[Image Source: Microsoft Docs, B2C Sign up configuration]
What are the features of Azure AD B2B?
Business collaborations online have become basic but the threats are ever-increasing with increasing technology. Suppose you have some new employees to your organization to a particular department. So, Azure AD B2B is here to help you with your business collaborations along with multiple security levels.
- You can invite other businesses to collaborate with you by inviting them through Azure AD B2B authentication.
- Then you can assign to them a particular security role that seems appropriate to you and also assign a license to them for authentication.
[Image source: Microsoft Docs]
All these in just a few simple steps. But then there is this very important question – do they also need to have Azure AD credentials? Well, no.
They can sign in to your environment through your invite using their own credentials. This is a very handy feature that saves you from the hassle of creating a new account temporarily and password for it.
Bulk Invitation
Apart from single collaborations, many times you need to invite a large group of people and not just a single person? For example, you might have just entered into partnership with a new organization and all their employees will work in your organization.
So, for a large number of people you can’t just carry out the same process, isn’t it? There’s a solution to this also. For inviting a bulk, you can simply install and use Azure Active Directory PowerShell by visiting the following link:
https://www.powershellgallery.com/packages/AzureADPreview/2.0.0.98



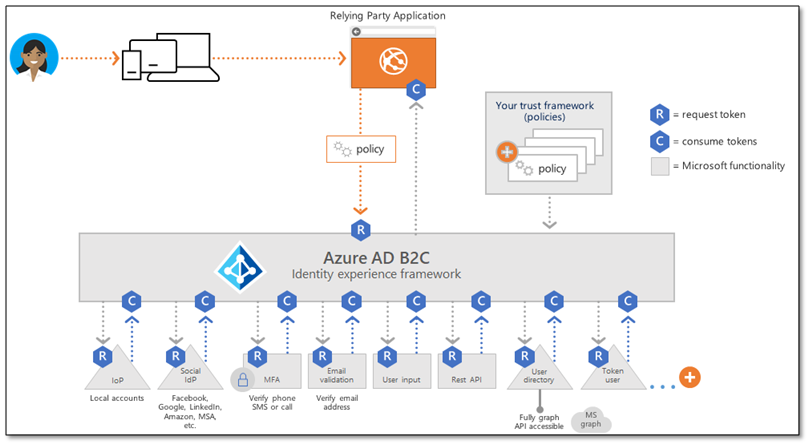
We looked at only the business collaboration side until now. Service/application users are great and the most important part of your business, isn’t it? Hence, B2C authentication has been designed for you keeping this as the primary focus. The primary features of Azure AD B2C are:
- Sign-up and sign-in through an existing account from a different service provider.
- Customized login process for a personalized experience.
- Easy scalability and security.
- Can be assigned administrative/security roles.
It is a different service that creates a repository for customer identity, apart from the user repository (B2B), and provides them easy access to your offered services.
- You can allow your customers to log in through their already existing identity from a different service provider than Azure, including social accounts.
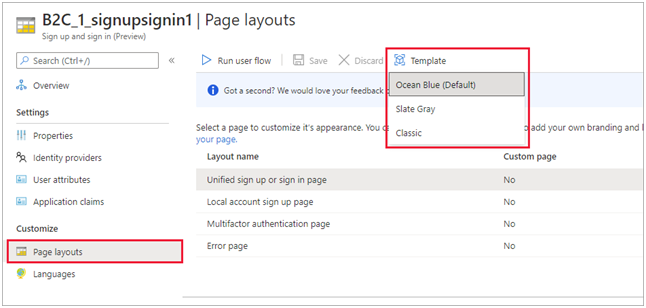
- You might have observed that people tend to use services that seem more friendly and intuitive to use and navigate. So, for this, Azure AD B2C allows you to create a user-friendly interface to let them enter their credentials for sign-up and sign-in.
- The customer journey can be customized, as you want, through Azure AD B2C. This data can be stored in the cloud and retrieved every time the customer visits and sign-in to your website. This facilitates you to provide your users to get a customized experience.
- You can also give access to tenants as an administrator role or limited access to tenants. This would be similar to B2B authentication.
- This would definitely attract a greater number of users to your service portals. Azure AD B2C also keeps into account the security and scalability factor for your organization.
Now, as you are better aware of the features of both the authentication type, why not get to know the ease of process in brief for respective authentication types?

[Image source: Microsoft Docs]
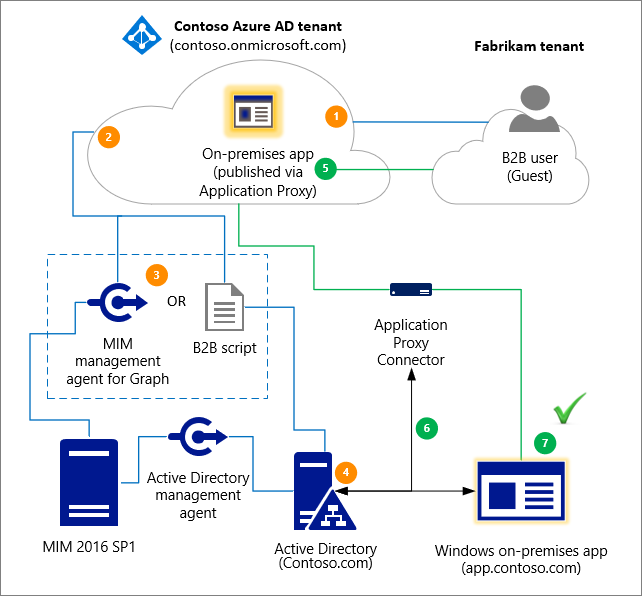
Authentication process of Azure AD B2B
As the admin of your organization, you can invite users using three different methods and set up different levels of security roles.
- You can invite the other users to your environment that has a security group.
- You can permit users to your environment not to have a security group.
- You can also invite a bulk of guest users using a .csv file with just a few clicks.

[Image source: Microsoft Docs]
You can refer to the detailed steps in the following Microsoft Guides to get started.
Add B2B collaboration users in the Azure portal – Azure AD | Microsoft DocsB2B collaboration code and PowerShell samples – Azure AD | Microsoft Docs
Authentication process of Azure AD B2C
As stated earlier itself that B2C is a more suitable way for collaborations online. Let us look at the authentication process and specifications for Azure AD B2C in simple terms and determine why it is useful for your organization.
Azure AD B2C provides different kinds of user accounts that can be categorized as the following:
- Work account -These are the users with work accounts are given permission to manage resources in a tenant, and permitted to an administrator role, they can also manage tenants. They can create new consumer accounts, block/unblock accounts, reset passwords, and set permissions or assign an account to a security group.
- Guest account – You can invite external users to your tenant as guests. An example of such a scenario for inviting a guest user to your Azure AD B2C tenant is when you share the administration responsibilities.
- Consumer account – You can let the consumer create an account on your portal through your Azure AD B2C directory. You can let users complete the sign-up user journey in an application you’ve registered in your tenant and allow this customer journey to get completed in various steps after every sign-in by recording the different activities.

[Image source: Microsoft Docs]
Multi-Factor Authentication
For B2C accounts if you want to let users access your sensitive/other important applications then they should have Multi-Factor Authentication (MFA) enabled to address the security issues (for example, verification of phone number). This is a good way to ensure an extra layer of security for them and for your organization.
Now, that you have the knowledge of not only the features but also the overview of the procedure, what do you think what suits you best? You must have got somewhat a clear answer. So, let me take you to the last part and put an end to the little doubt you may have.
Deletion of B2B and B2C accounts
When a B2B account is deleted, the user cannot access it and it is completely managed by the host. However, the lifecycle of a B2C account is not managed by the host, rather it is managed by the user itself or the application. So, the user can decide when to stop using the services of a particular organization but still be able to access it using their account.
B2C accounts don’t need the user to be associated with the organization. Hence, if at some point a user was associated with the organization and later on, they leave, still they would be able to use their B2C account for the services available to the outside user.
Comparing B2B and B2C at a glance


Conclusion
In B2B you need to send an invite to the collaborating parties. In B2C the customers/users just need to sign up on your portal with any identity and their credentials of that service provider.
In B2C, you don’t need to get worried about password resets, scalability, and security of bulky data, it is taken care of by Azure AD services automatically.
So, clearly, B2C authentication has an edge over B2B authentication.
So, you can just compare all the major differences between B2B and B2C at your fingertips now. Hope it helps!





